How Hackers Evade Malware and Anti-Phishing Blacklists
By Erhan on April 24, 2017
Hi Morty,
On Friday 07 April 2017 your credit card ending in XXXX was stolen by the website
whatsappsubscribers.com which is a scam site pretending to be WhatsApp.
Additional personal information including your full name, date of birth,
telephone number, email, home address, card expiration, and card CVV was also
stolen.
I highly suggest contacting your bank and cancelling your card immediately. Ask
your bank about putting a Fraud Alert on your credit report. You should also
strongly consider filing a police report.
You may be wondering how I know about this. I run a cybersecurity company that
creates a free browser extension for Chrome called NoHack that stops and tracks
these kinds of scams. In our own systems, I noticed this site was flagged and upon
further investigation discovered a list of victims containing your information. I
felt a moral obligation to quickly inform you before further damage can be done.
I'm sorry this happened to you and hope nothing more comes of this. Every morning for the last few weeks, I've been sending out this email to a list of victims in a carding scam we discovered targeting WhatsApp users in the UK thanks to people using our NoHack chrome extension.
Despite our efforts to get the site blacklisted in various sources like Google's Safe Browsing and PhishTank, it remained online for months. Each day had at least 3 new victims.
This kind of scam is nothing new, but what makes this scam so interesting is how it managed to stay online with very little effort, or sophistication.
It's unsophisticated because this is how simple the attack is:
1) The attacker sends out an SMS or email similar to this:
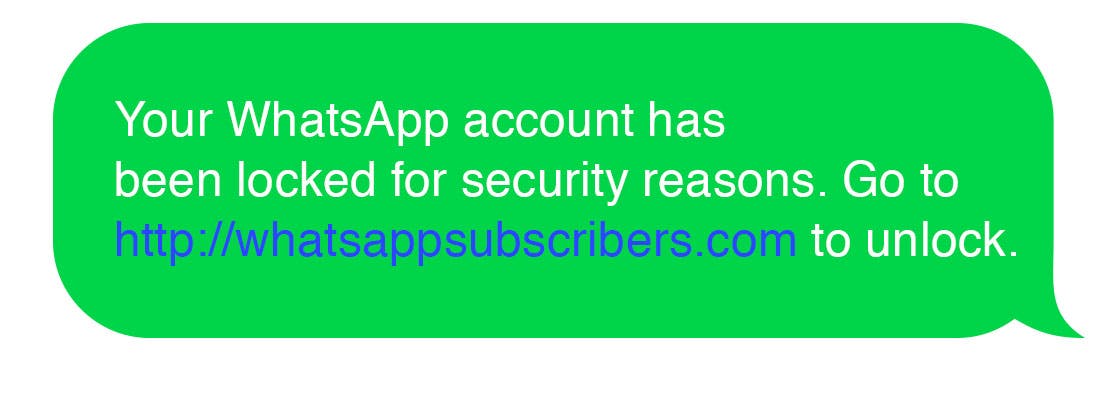
2) The victim enters personal information like credit card details, date of birth and security answers.
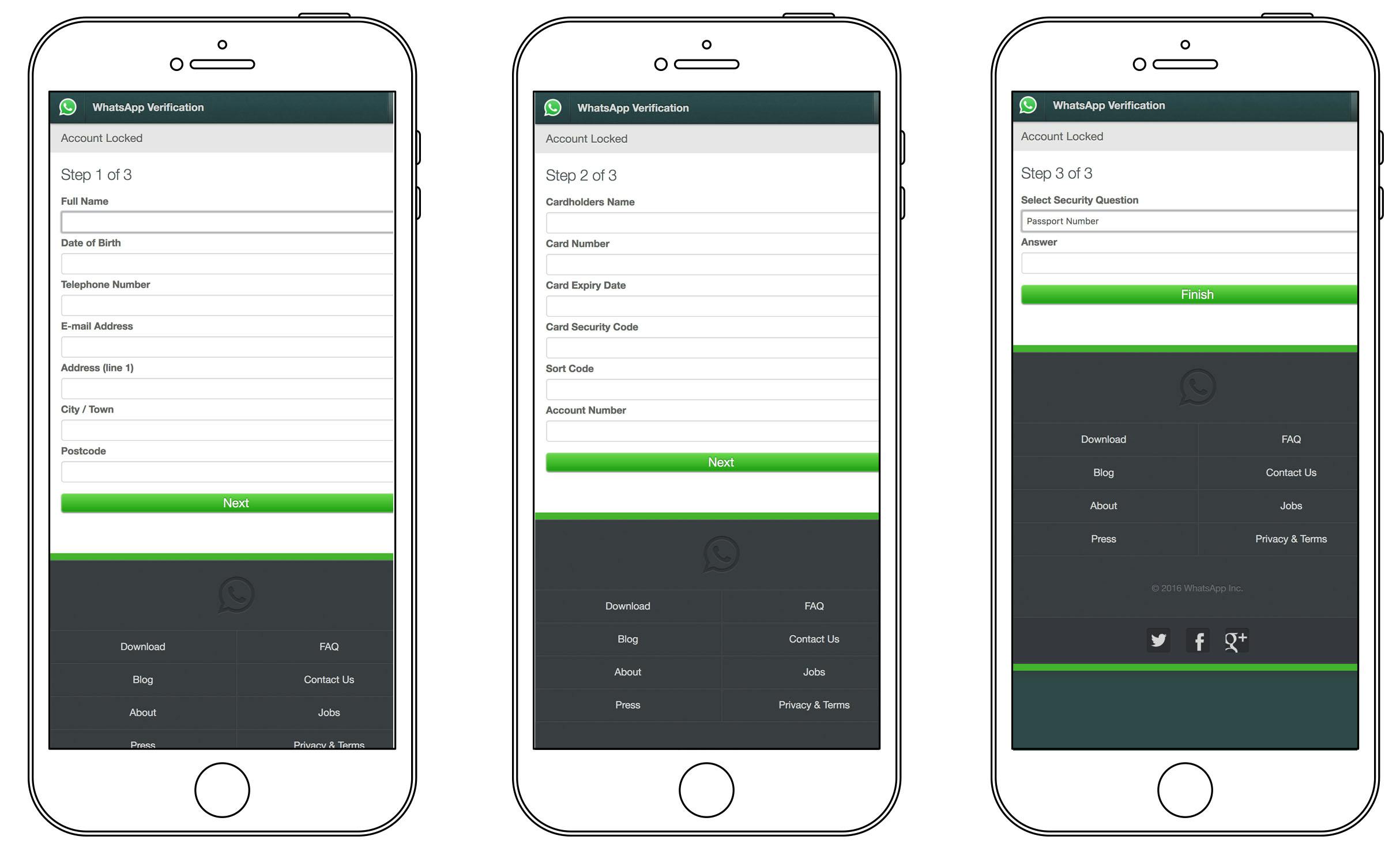
3) The scammer receives an email with all the info that looks like this:
+ ------------- Data Compromised -------------+
+ ------------------------------------------+
+ Personal Information
| Name : Morty Smith
| Dob : 01/09/2003
| Telephone : 012345678912
| Email : morty.smith@getschwifty.com
| Address : Earth (Dimension C-137)
+ ------------------------------------------+
+ Billing Information
| Card BIN : 000000
| Card Bank : Galactic Federation
| Card Type : DISCOVER
| Cardholder Name : Morty Smith
| Card Number : 6011318314693334
| Card Exp : 01 / 21
| CVV : 000
| Account No : 00000000
| Sort Code : 00-00-00
+ ------------------------------------------+
+ Security Information
| Mothers Maiden Name : sanchez
+ ------------------------------------------+
+ Victim Information
| Submitted by : 94.142.241.111 (galactic.federation.earthlink.com)
| Location : Earth (Dimension C-137)
| UserAgent : Mozilla/5.0 (Linux; Android 6.0.1;)
| Browser : Chrome
| Os : Android
| Received : Tuesday 11 April 2017 @ 15:47
+ ------------------------------------------+This site was online from September 2016 to April 2017 until we finally got the hosting provider to ban it. It took them several weeks while the site actively evaded blacklists.
While the site was online, we were able to determine the following attack statistics:
- 3-5 victims per day
- Average Victim Age: 56
- Attack Reach: At least 9k
- Cards Stolen: 700+
- Attack Conversion: At least 8%
- Corporate emails used 12% of the time in victim sample
Visitors by Operating System
Windows: 3399, iPhone: 1959, Android: 1506, OSX: 1029, iPad: 114, Other: 367
If we assume each victim loss is about $250.00 that's a loss of at least $175,000. That's crazy considering the scam was probably done automatically with a press of a button.
In fact, I know the scammer was lazy because I was able to get the above statistics from the site's homepage:
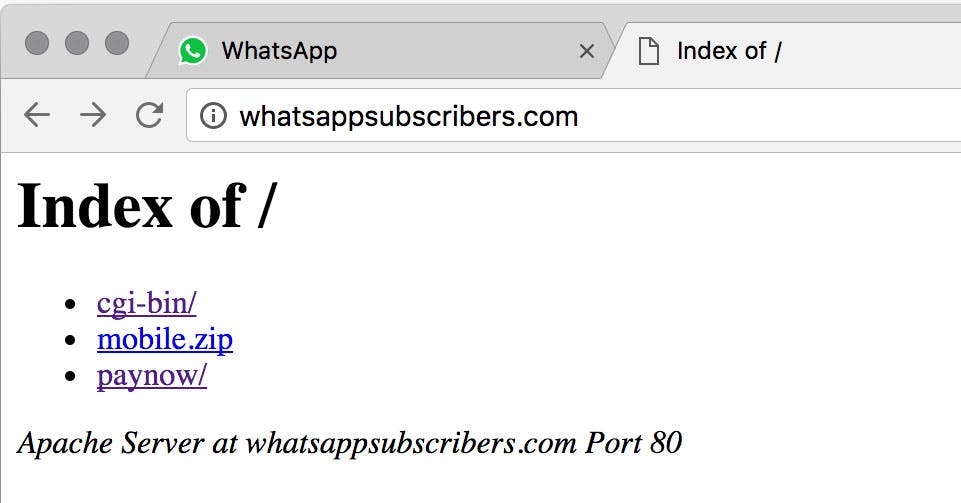
What you are looking at is the code for this scammers's site including snippets of the victim information accidentally left out in the open for everyone to see. The file mobile.zip hilariously contained the attack code, which I was able to use to see more exposed data and resources.
The code was in PHP and was rather simple, it featured:
- AES 256 encryption of results
- Abuse and profanity filter (you can't spam results)
- Rate throttling (you can't DoS the endpoints)
- Control and session protection
- Email result configuration
Pretty neat stuff, but the secret sauce that allowed it to stay online for so long was it's anti-blacklisting functionality. This feature had three main components:
- Behavior analysis based on geolocation, browser fingerprinting, and one time access (which blocks an IP after multiple visits)
- Domain priming where the attack page checks it's own IP reputation
- Adblock like subscription with an auto-updating blacklist to block security companies
Yup, that means anti-phishing and malware blacklists are not nearly as effective as we think they are. When a security service scans the internet and finds a malware or phishing site, it can't differentiate between a real attack site and a fake attack site.
Hackers lure security services into fake attack sites to build a security service blacklist. When a real attack site encounters a blacklisted security service, it shows a completely different page, allowing it to fly under the radar. Basically, a blacklist to blacklist the blacklisters.

Here's the blacklisted services from this scam:
- NETCRAFT
- KASPERSKY
- OPENDNS
- INTERNET SYSTEMS CONSORTIUM ( PHISHTANK )
- BITDEFENDER
- SURFRIGHT
- FORTINET TECHNOLOGIES
- GOOGLE APPS
- TOR SERVERS
- AMAZON
- OVH
- RACKSPACE
- JAPAN NETWORK INFORMATION CENTER
- HOSTING SOLUTIONS UKRAINE
- NEW DREAM NETWORK
- RCS & RDS RESIDENTIAL
- TORNET
- ROMTELECOM
- NETPILOT ( CLEAN-MX.DE )
- DATAPIPE
- PEER 1 NETWORK
- ANEXIA
- LEXSI
- FASTWEB ITALY
- GOOGLE CHROME
- ADNET TELECOM
- MCAFEE IP RANGE
- HOSTWAY ROMANIA
- NOISEBRIDGE
- QUBE MANAGED SERVICES
- FORMLESS NETWORKING
- CHAOS COMPUTER CLUB
- MICROSOFT SINGAPORE
- ALIENVAULT
- AVIRA
- COMODO GROUP
- AVG TECHNOLOGIES
- ESET
- DOCTOR WEB
- PANDA SECURITY
- SYMANTEC
- INETU INC
- ABOVENET COMM.
- LEVEL 3 COMM.
- INTERNAP
- INTERNET IDENTITY
- RELIANCE INFOCOM INDIA
- MICROSOFT
- G-DATA SOFTWARE
- SOPHOS
- DATATRAN SYSTEMS
- NETSUMO
- THE NEW YORK INTERNET COMPANY
- TECHCREA SOLUTIONS
- SOLUTIONPRO INC.
- MOSCOW LOCAL TELEPHONE NETWORK
- MAXIS BROADBAND MALAYSIA
- 2COM CO
- POWERTECH INFO SYSTEMS
- LINODE
- ARUBA S.P.A.
- MASSACHUSETTS INSTITUTE OF TECHNOLOGY
- INTEGRA TELECOM
- ZWIEBELFREUNDE ( TOR EXIT NODES )
- AT&T
- MALCOVERY SECURITY
- TIME WARNER CABLE
- OPAL TELECOM DSL
- BEZEQINT BROADBAND
- UNSPAM TECHNOLOGIES
- HURRICANE ELECTRIC
- TELUS COMMUNICATIONS
- NEOSTRADA ADSL
- MAROCTELECOM
- HOSTDIME
- HETZNER ONLINE
- MICHEAL MCDONOUGH
- JIFFYBOX SERVERS
- THEPLANET.COM
- EDION CORP.
- FHCDMA WIRELESS NETWORK
- ONEANDONE INTERNET
- RACKSPACE CLOUD SERVERS
- ADRIAN HALMAGYI
- CORBINA TELECOM
- PSINET INC.
- RUTGERS UNIVERSITY
- EBAY INC.
- UROSPACE
- ADATPARK
- VIAWEST
- TOR EXIT NODES
- SOPRADO GMBH
- RELIABLE WEB SERVICES
- SWISS PRIVACY FOUNDATION
- UBIQUITY SERVER
- SECURE DRAGON
- INTERGENIA
- A1COLO
- BT UK
- CHINANET
- KEYWEB
- FDCSERVERS
- LEASEWEB GERMANY
- EUSERV.DE
- A100 ROW
- MICROSOFT
- WEHOSTWEBSITES.COM
- ANTISPAM EUROPE
- YAHOO
- MOSCOW COLOCATION
- HOSTMASTER LIBERTY GLOBAL
- GOOGLE CLOUD
- OPERA
- INDIAN ISP ( MICROSOFT/GOOGLE-RELATED )
- GODADDY
- CORPORATION SERVICES WORLDWIDE
- NETVISION
- GOOGLE CLOUD
- TRUSTWAVE HOLDINGS
- WEBSENSE-NET2
- Internap Network Services Corporation
- DomainSONOCrawler
- VERISIGN
- Trend Micro Incorporated Japan
- TI RUSSIA
- Domaintools, LLC
- Ovh Hosting, Inc - CANADA
- Latisys - Denver, LLC
- RACKSPACE : PART 2
- The Calyx Institute
- Datasource Ag : Switzerland
- Net By Net Holding Llc : RUSSIA (too many to list)
- Global Frag Networks
- United Networks of Ukraine, Ltd
- Prescient Software, Inc
- Fireeye, Inc
- Boston University
- Carnegie Mellon University
- Codero
- Abovenet Communications, Inc
- Golden Lines : Israel
- China Internet Network Information Center
- Handy Networks, LLC
- Bezeq International : Israel
- Fieldtech Inc
- Ovh Sas : France
- Ovh Sas - Germany
- Energy Group Networks Llc
- Amazon.com, Inc
- Powertech Information Systems As : Norway
- Netvision Ltd : Israel
- Rcs & Rds S.a - Romania
- Ovh Sas - Lithuania
- Ficolo Cust. 1158 - Finland
- Zhejiang Taobao Network Co. Ltd
- SOLAR-VPS
- Chinanet Jiangsu Province Network
- YBV : China
- Microsoft Corporation
- Aliyun Computing Co. Ltd : CHINA
- Versaweb, LLC : USA
- Fop Tokarchuk Oleksandr Stepanovich : UKRAINE
- Chinanet Fujian Province Network
- Bluehost Inc : USA
- National Cable Networks : RUSSIA
- Hostgator.com Llc : USA
- Green House Data, Inc : USA
- Hetzner Online Ag : GERMANY
Some interesting tidbits. TOR exit nodes are blocked and Noisebridge and CCC (popular hackerspaces) are blocked too.
Additionally, the scammer can use a whitelist strategy to block everything except users of certain internet service providers. For example, Vodaphone users in the UK.
So why are we able to discover and stop this attack where other tech giants have failed?
We are able to accurately assess malware and phishing behaviors from only a few tracked samples provided by our small community of NoHack users via One-Shot Learning. We don't rely on blacklists and we don't have to scan the web.
For now, I want to thank our small community of users who saved numerous individuals from credit card fraud. Here are some of the Thank You replies I received.
Dear Erhan,
Thanks very much for the tip off. I contacted the credit card provider and we spotted
fraudulent attempts to use my card today. The card is now cancelled and will be
re-issued, so thanks again for your vigilance and for alerting me -- it's much
appreciated. Thank you so much. I called the bank and cancelled the card, although I am not sure
about the value of the other information I provided. Does your app work in Safari? Erhan,
That is very kind of you to reach out and let me know. Other than cancelling my
card, is there anything else I need to do? Still not blacklisted, but it's finally offline.
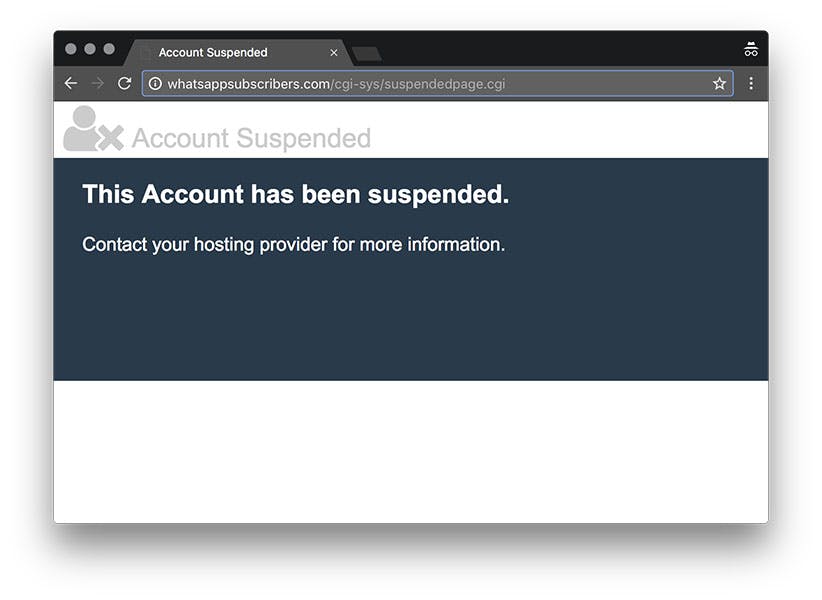
...unless that's a fake page and I've been blacklisted too ;)
About Apozy
Founded in April of 2014 in San Francisco, we are a venture-backed motley crew of passionate hackers building cybersecurity technologies to make the world's information faster, cleaner and safer to access.


