Inspect the Web without Breaking It: SSL Inspection for the Future
By Rick Deacon on June 15, 2020
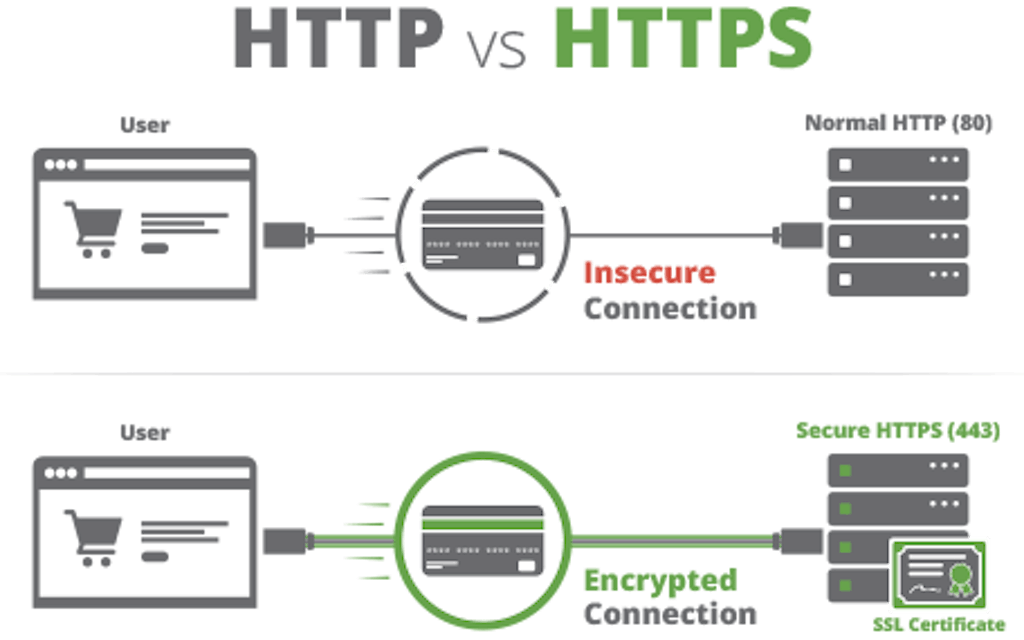
SSL Inspection or HTTPS Inspection breaks SSL encrypted internet communication between the client and the server. The interception is typically done on the server and its purpose is to see “inside” encrypted web traffic. Legacy security applications block millions of SSL encrypted messages that contain advanced threats everyday, so without inspecting it, data around those attacks is limited.
SSL encryption is sophisticated but not perfect. When a client, such as a browser, first sends an HTTPS request to a Web server, it starts a series of message exchanges called the SSL handshake. During the SSL handshake:
- The server sends its digital certificate to the client to authenticate itself.
- The client and server agree on the SSL protocol version and algorithms to use.
- The client and server generate the symmetric keys they will use to encrypt their messages.
While this protects most everyone from cleartext theft and other dangers online via encryption, it also means that dated security tools must break SSL via a method called SSL inspection.
Traditional SSL inspection enables organizations to intercept user HTTPS requests, break the encryption, determine that the server is legitimate, and create a tunnel between the user and the server. This process is hardware intensive, often breaks websites, and makes browsing slow. Most importantly, it destroys a security protocol which has been widely accepted as being one of the most significant ways to increase web security globally.
Cost and performance have been the primary limitation for fully implementing SSL inspection. Concerns about privacy also come up. Obviously, the move to SSL for the entirety of web traffic is not slowing down. Ultimately, these concerns must to be mitigated.
One way to mitigate the concerns of breaking SSL and things like DNS over HTTPS, which will prevent DNS tools from even seeing traffic, is to stop decrypting SSL traffic altogether. In order to do that, you’ll need to move data collection to the browser. Within the browser, an extension has the ability to read and collect data from malicious websites and traffic, enabling the same level of insight gathered from SSL inspection. Those data points are delivered in real-time, enriched with user information but without the slowdowns, heavy cost, and broken pages.
Using an extension like Airlock enables organizations of any size the ability to see traffic “behind” SSL without concern of changes to SSL breaking their existing security tools. Airlock deploys in under a minute to every browser in your organization and immediately begins logging traffic. Employees and users of Airlock will notice no difference in their browsing but administrators will quickly glean the data they’ve been waiting for without any of the caveats.
Using browser-collected data future proofs your security stack and prevents user experience problems. In order to maintain your security posture and enable your security team to keep working when things change, it’s recommended that companies consider moving their “behind” SSL data collection to client-side methods before 2021.
About Apozy
Founded in April of 2014 in San Francisco, we are a venture-backed motley crew of passionate hackers building cybersecurity technologies to make the world's information faster, cleaner and safer to access.