Remote Browser Isolation VS Native Isolation: What’s the difference?
By Rick Deacon on July 24, 2020
Browser Isolation is a relatively new technology, growing in popularity in 2019 & 2020, expected to be an even larger part of the security stack in 2021 and beyond, according to Gartner.
What is Browser Isolation?
The purpose of the technology is to create an “air gap” between the user’s browser and the internet, keeping them safe from online attacks like malicious downloads and phishing.
There are multiple types of isolation but the two most common are remote browser isolation and Native Browser Isolation, that bridges the gaps between Local and Remote Browser Isolation.
Many companies are exploring the technology to fit into their own business, but are confused on what the benefits of each technology are.
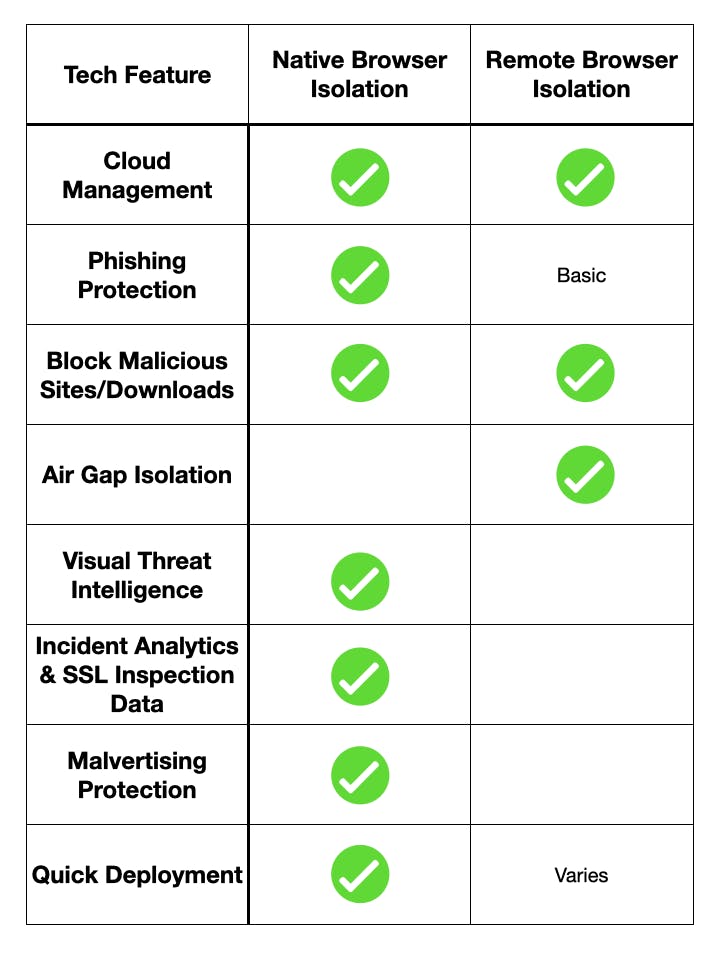
Remote VS Native Browser Isolation — Technology Differences
Remote browser isolation creates an air gap by streaming the internet to the end user’s browser, usually from the cloud. The services typically load a page off-site, re-render it, and stream it to the browser. This removes anything malicious embedded in the page like scripts and prevents all downloads — dangerous and safe alike.
There are a few downfalls with this type of solution. Typically, it breaks user experience. Sites that are rendered client-side are unlikely to render correctly in a remote browser isolation solution. Examples of client-side rendered sites are Facebook and YouTube. Remote browser isolation companies have solved this by writing exception lists that don’t re-render those pages, excluding them from any protection or isolation.
Data is also not retrieved from remote browser isolation solutions. They do not collect data for privacy’s sake, but there’s also no way for them to collect browsing or incident data.
The most prolific type of browser-based attacks are phishing and social engineering, which are not covered by remote browser isolation. Some companies use a basic threat intelligence filter list which has been previously verified and is hours or days old, not able to protect against spearphishing or advanced attacks like 2FA bypass or malvertising.
Native Browser Isolation is cloud based and uses technology existing in the browser to create a sandbox that stops malicious sites, downloads, scripts, and ads. Detection for malicious pages is done via visual artificial intelligence and machine learning. Native Browser Isolation reports data similar to SSL inspection proxies but without a gateway or breaking SSL/TLS.
Unlike remote solutions, native isolation does not change user experience, as it makes malicious pages read-only instead of blocking or rewriting them. It removes the need for exception lists and mitigates false positives.
The visual AI component detects malicious pages at time of click, preventing all social engineering and phishing attacks as well.
Additionally, centrally managed adblocking is the only method of preventing malvertising attacks, as deployed within Native Browser Isolation.
Native Browser Isolation was created to fill the gaps found in remote browser isolation. The technology is different because Native isolation does not create an actual air gap. The browsing experience remains the same, but with added protection to create isolation for the web browser.
Use Cases
Remote and Native Browser Isolation have different use cases.
Remote Browser Isolation Use Case A very large financial institution uses remote browser isolation to ensure 80,000 global employees are protected from all downloads that could be malicious. Those employees use endpoints to process information and access cloud applications, meaning they have very little need to download files from the web or visit YouTube. Their user experience when browsing is different than they’re used to, but they are protected against downloads that could infect their machines or network.
Native Browser Isolation Use Case The largest US-based cryptocurrency exchange with 1,500 global employees use Native Browser Isolation to ensure that employees retain the browsing experience they expect while being protected from malicious downloads and targeted spearphishing attacks. Advanced, technology-forward organizations like crypto exchanges need to collect browsing data without breaking a security protocol, so they use native isolation to accomplish that to collect browsing information. They chose Native Browser Isolation to make deployment and management very simple and reduce stress on their team. Click here to find out more about Native Browser Isolation.
Which is right for you?
Both forms of isolation can be very useful platforms. Deciding which one to use depends on your goals, but there is some overlap between the two platforms.
Use remote browser isolation if you need a physical air gap as part of a compliance or policy requirement. Typically, this would be larger organizations with over 10,000 employees.
Use Native Browser Isolation if you need protection from advanced phishing, incident information, and to keep the user experience of standard browsing intact. This would work best for organizations with 150 to 10,000 employees.
Ultimately both have their purpose. In the author’s opinion, remote browser isolation is a better fit for large, legacy companies and Native Browser Isolation fits the model of a fast-paced growing organizations.
About Apozy
Founded in April of 2014 in San Francisco, we are a venture-backed motley crew of passionate hackers building cybersecurity technologies to make the world's information faster, cleaner and safer to access.

